| Information and assignments about |
| DES, the Data Encryption Standard |

We will discuss DES in class on Wednesday, April 19. Be prepared to talk about and ask about the topics below.
|
Write a paper between one and two pages long about the Data Encryption Standard (DES) and its policy implications. The paper is due Wednesday, April 26. I suggest that you write about one of the topics above. Explain any technical terms you use carefully with standard English words and sentences. |
You may certainly look for information on your own. Below is a short list of relevant links I've compiled. A web search certainly will yield many more links to consider.
| Some quotes | Introducing DES | Breaking DES |
| NIST and DES | NIST and AES | General background |
Some quotes
| Security is little more than economics. A cryptographic system is secure when it costs more to break it than the data it is protecting is worth. Accordingly, determining the strength of an encryption algorithm comes down to measuring the cost of the cryptanalytic resources needed to break the system. That explains the basic need for an evaluation of the cryptanalytic performance possible today. |
| It is easy to be paranoid when it comes to encryption, but keep this in mind. It is in the US Government's interest to provide a good encryption standard. If the NSA could read industrial and technology secrets protected by DES than so could the KGB. It is my opinion that DES was designed to balance the competing interests of a government reading its citizens' secrets and being sure that no other government could read them. I believe that this resulted in an algorithm of very high security, but one that can be broken through brute force by a truly massive assault. The inevitable march of technology has slowly eroded the amount of technological know-how needed to break DES but the hurdle remains high for the next decade or two. |
Back to the link
index
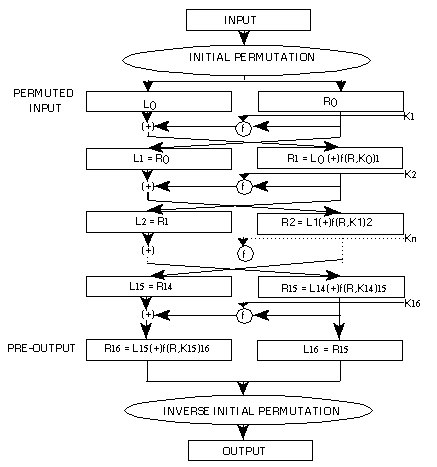
Introducing DES
Back to the link
index
Breaking DES
| http://www.eff.org/descracker/ | ||||||||
| The Electronic Freedom Foundation's web page about "cracking DES": many links to press releases, news articles, etc. about the cheapest, fastest publically known way of cracking DES. | ||||||||
| http://www.cryptography.com/des/despictures/index.html | ||||||||
| Pictures of the cracking machine. | ||||||||
| http://www.interhack.net/projects/deschall/what.html | ||||||||
| A discussion of ``cracking DES'' by exhaustive search. It describes how such a search can be distributed over the net. This was the most widely publicized method of breaking DES before the machine described above was constructed. | ||||||||
| http://www.interhack.net/pubs/des-key-crack/ | ||||||||
| A more technical version of the article above including such figures as ``keys searched per day''. | ||||||||
| http://cryptome.org/cracking-des.htm | ||||||||
| The introduction to the book about cracking DES. It includes useful general information on such efforts and introduces some policy questions. Especially interesting for this class is the first section of the first chapter, "The Politics of Decryption", which people should read to encourage their paranoia. One chapter of the cracking book discusses the politics and legalities of publishing a book on cracking DES. Chapter 10 of the book is independently available. It is quite technical, but discusses how to break DES, A4 (the algorithm formerly used for security of European cell phones -- but the replacement algorithm, A5, currently used in GSM cell phones, has been documented as quite easily broken!) and RD4 (the bitstream generator widely used for electronic commerce). | ||||||||
Back to the link
index
NIST and DES
| The agency was established in 1901 as the National Bureau of Standards. ... NIST strengthens the U.S. economy and improves the quality of life by working with industry to develop and apply technology, measurements, and standards. |
| Data can be recovered from cipher only by using exactly the same key used to encipher it. Unauthorized recipients of the cipher who know the algorithm but do not have the correct key cannot derive the original data algorithmically. However, it may be feasible to determine the key by a brute force "exhaustion attack." Also, anyone who does have the key and the algorithm can easily decipher the cipher and obtain the original data. A standard algorithm based on a secure key thus provides a basis for exchanging encrypted computer data by issuing the key used to encipher it to those authorized to have the data. |
Back to the link
index
NIST and AES
| It is intended that the AES will specify an unclassified, publicly disclosed encryption algorithm available royalty-free worldwide that is capable of protecting sensitive government information well into the next century. |
| An analysis of the algorithm with respect to known attacks (e.g., known and chosen plaintext) shall be included. In addition, all known weak keys, equivalent keys, complementation properties, restrictions on key selection, and other similar features of the algorithm shall be noted by the submitter. If no such values are known, then this shall be stated by the submitter. |
| The submitter should provide any mathematical rationale for the non-existence of trap-doors in the algorithm, to the greatest extent possible. |
Back to the link
index
General background